If you need to transfer information to or from a security sensitive network a firewall should not be the only solution you chose to enhance your cybersecurity. Though a firewall strives to protect the network, a high assurance addition in terms of a Cross Domain Solution is also needed.
What is a firewall and when is it not enough?
A firewall is a device with the purpose to protect your network by only allowing certain traffic to enter it. It monitors and filters what packets enter the network, and which are blocked based on rule setups. However, if you need to transfer information to or from a security sensitive network a firewall should not be the only solution you chose to enhance your cybersecurity. Though a firewall strives to protect the network, a high assurance addition in terms of a Cross Domain Solution is also needed.
Network segmentation and zoning
In today’s connected world, no system is stronger than its weakest link, and no critical information or system is secure if there is insufficient protection. A cyberattack can result in sensitive and/or critical systems being disrupted, knocked out or leak information. This means that by using zoning, one gathers assets with similar security level and security requirements in separate zones. Segmentation means that you have separate zones for your assets, but most often, you still allow some communication between these zones. In some slightly more extreme cases, isolation or air-gap may be relevant, and then no network-based communication between the zones is allowed. The most critical systems, or the most sensitive information, must be protected with high-assurance solutions in order to obtain a high level of security. A secure way to protect your sensitive information or systems is to start working with network segmentation.
Read more about network segmentation and zoning in our Use Case!
What is a Cross Domain Solution?
Cross Domain Solution (CDS) is a term used to describe the concept of maintaining secure information exchange between domains with different security or protection needs. This can be between databases, servers, applications, or combinations of these.
CDS addresses the concept of communicating, sharing or moving information between domains and applies validation, transformation or filtering to the exchange.
How does a Cross Domain Solution work?
Cross Domain Solutions include three types of information exchange principles:
- Bidirectionally to tailor information exchange.
- Unidirectional for ensuring integrity or confidentiality of domains.
- Airgap between systems using manual transfer and control of the information.
Bidirectional information exchange
Bidirectional gateways allow for a strictly controlled two-way filtered information flow. It uses filters in both directions and information is always controlled using full message inspection. The filter can allow information to pass depending on several factors e.g. source/destination addresses, file formats, attributes or the presence of a digital signature.
Unidirectional information exchange
For unidirectional information exchange, a data diode can be used. Guaranteeing a unidirectional flow of information means sensitive information can be transferred without jeopardising the integrity or the confidentiality of the network, depending on how the data diode is used. Another benefit lies in the technology of a data diode. Being hardware and not software based means it cannot be attacked by malicious code and intrusion is thereby prevented. A data diode allows you to transfer the data without putting the security of the network at risk.
How do I enhance the network security level?
If you have security sensitive or even classified information, you need a viable Cross Domain Solution that offers secure and filtered bidirectional communication. The purpose is to apply strict information-level control during information transfers and mitigate cybersecurity threats such as manipulation, data leakage and intrusion. Advenica’s solution is ZoneGuard. ZoneGuard is not a substitute for a firewall but instead it enhances the overall network security level. This solution enables digitalisation without compromising security and at the same time is flexible and simple to adjust to the different needs of your organisation.

What is the difference between a Security Gateway and a firewall?
A Security Gateway can be compared to a firewall as it regulates what traffic that can enter and exit a network. A comparison to explain the difference between a Security Gateway and a firewall could be to visualise an airport. The firewall would be the check-in desk where a simple check is performed, such as identity and ticket control. The Security Gateway would be the security control where you are more scrutinised, your bags are looked through, you go through body visitation, and so on.
A firewall is a device with the purpose to protect your network by only blocking known bad traffic to enter or exit. It monitors and filters what packets are blocked based on its configuration.
For some types of businesses, a firewall is simply not enough.
With a firewall, it is difficult to know exactly what information is being exported or imported into the system. A firewall configuration often becomes complex, which increases the risk of misconfiguration. Firewalls also do not separate administration and data flow in a way that protects the information from insiders. Organisations that have sensitive and confidential information and that operate in critical infrastructure, public sector or the defence industry, need their networks to keep a higher level of security. That is why additional solutions to a firewall are needed.
What is a ZoneGuard?
ZoneGuard is a security gateway that controls the information exchange that takes place between different networks and security domains. ZoneGuard focuses on information flow and ensures that organisations’ information policies are enforced during every transfer. ZoneGuard also creates an audit trail providing evidence of all transfers.
How does a ZoneGuard work?
ZoneGuard allows for a strictly controlled two-way filtered information flow supporting third party controls for enforcing a digitally signed information policy. ZoneGuard uses filters in both directions and information is always controlled using full message inspection. The filter can allow information to pass depending on several factors e.g. source/destination addresses, file formats, attributes or the presence of a digital signature.
What does the ZoneGuard process look like?
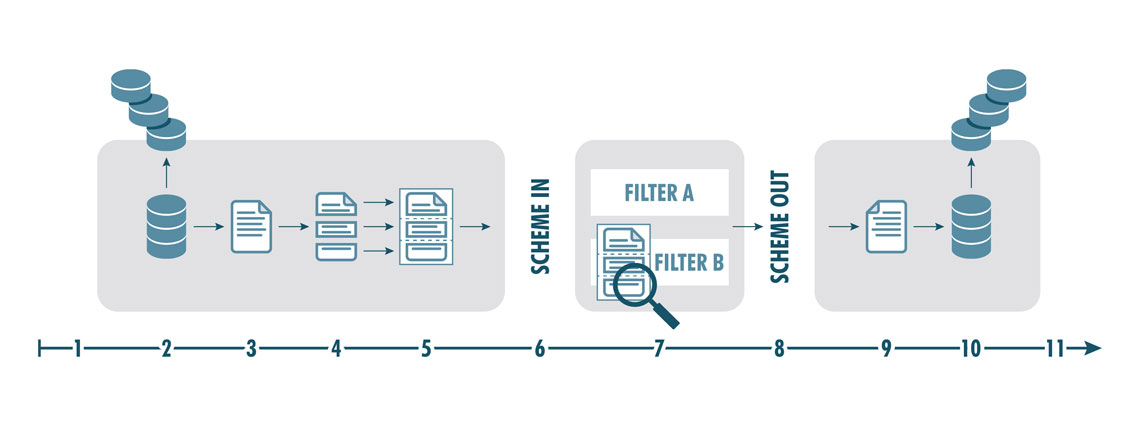
When a message is sent from one system to another where both systems are connected to a ZoneGuard, information in the message received from one system is analysed according to configured rules. Approved parts of the received message are put into a new message which is sent to the intended receiver on the other system.
- Data is sent to one of the DATA ports on the ZoneGuard.
- The data packages are collected.
- The entire message is restored.
- The message is divided according to the loaded Service.
- The content is structured to fit the loaded Schema.
- Schema In will accept only correctly structured content.
- Pre-defined filter checks the content.
- Schema Out will accept only correctly structured content.
- The entire message is restored.
- The message is divided into data packages.
- The data packages are sent to the intended receiver.
Why do you need a ZoneGuard?
There are many systems and solutions that are vulnerable to protocol or implementation errors. These potential vulnerabilities are e.g. flaws in a network protocol or applications that haven’t been tested enough for buffer overflow attacks. A ZoneGuard will prevent these by providing:
- Protocol-break to reduce the attack vectors dramatically by removing attacks on the network layer level.
- Transformation of network protocol and information content from one format to another mitigates malwares and application layer attacks.
- Validation and filtering of the information per an organisations information policy safeguards that only information permitted by you is transferred.
Who needs a ZoneGuard?
Cybersecurity threats today are diversified and the ZoneGuard technology has several defense mechanisms which all act together to provide protection for your information flow. ZoneGuard’s ability to safeguard which information is transferred to and from a system provides unparalleled control and accountability for any organisation with a critical information flow, whether you are work with national security, critical infrastructure or in the public sector.
What makes the information flow and filtering process within Advenica’s ZoneGuard unique?
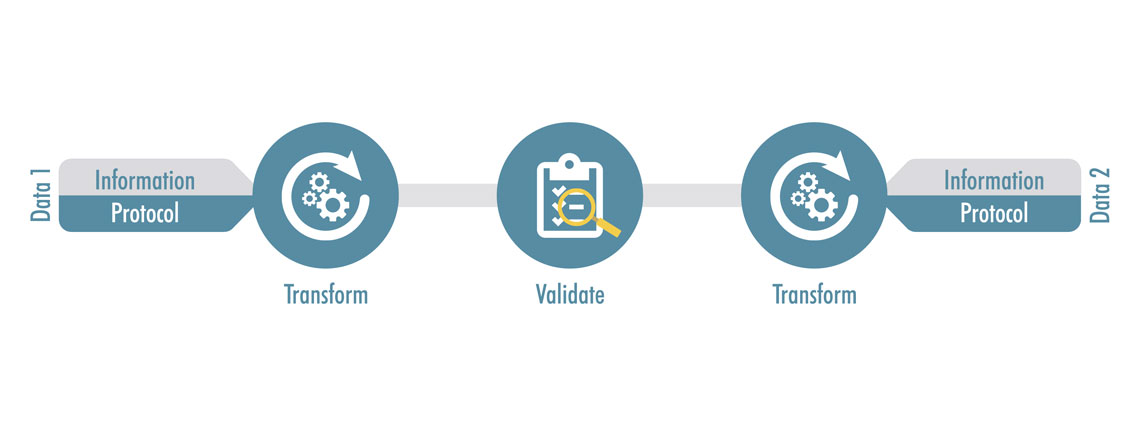
ZoneGuard enables protocol-independent, information-only forwarding. This occurs by separating the actual information from its delivery vehicle, only allowing the actual information content to be processed in the filter. Only required and permitted information content is allowed through. It prevents information that is not allowed per the policy to pass through the filter. After filtering, the relevant information is repacked into the required delivery vehicle (the same type of incoming delivery vehicle or another type). This enables you to securely exchange only permitted information between sender and receiver.
Nothing more, nothing less.
Read more about how ZoneGuard can be used in our Use Cases.




