Have you already secured your IT/OT integration? Congratulations! Then you have an advantage over many others, and you also have the opportunity to do several things that those who have not secured their IT/OT integration cannot even think of doing.
All you can do if you have a secure IT/OT integration
There are several things you can do if you already have secured your IT/OT integration:
Connect the OT environment to the cloud
The advantages of cloud services are many – here are some of them:
- You only pay for the capacity you actually use
- You can easily scale up or down as needed – and you get close to unlimited data processing and storage
- Cloud usage allows your employees to work anytime, anywhere, on any device, provided they have an internet connection
- The cloud is more flexible and thus reduces the investments required to start a new business and contributes to faster implementation of new IT services
- Always using the latest technology – the flexible, on-demand nature of the cloud means you can adopt advanced technology as soon as it hits the market
Make AI analyses of production data
AI solutions are used in the manufacturing process to automate and optimise tasks that were previously done manually. This allows companies to take a more data-driven approach to production, monitoring every step of the process to ensure accuracy and quality. AI can also be used to identify potential problems in the production process, allowing companies to act quickly and prevent costly delays.
AI solutions also help reduce costs in the manufacturing process. For example, AI powered robots can take on repetitive, low-value tasks, freeing up human employees to focus on higher-value activities. In addition, AI can be used to streamline certain parts of the work in the supply chain, such as material calls, purchasing, planning, etc., which helps ensure that materials and components arrive on time, which in turn reduces the risk of delays.
Continue your digitalisation journey
Digitalising means that you use the digital technology available on the market today to develop your business. In fact, the possibilities are basically endless, but often involve streamlining internal and external work processes.
If you have secured your IT/OT integration, you have taken a big step forward in your digitalisation journey and can, for example, work with preventive maintenance.
Preventive maintenance is planned maintenance to keep your assets running smoothly. Instead of reactive maintenance, preventive maintenance is performed at regular intervals to reduce the need for reactive maintenance. Calibrations and equipment checks are examples of preventive maintenance. These processes are critical because your assets are critical, so it is important to make sure they do not break down when you need them most. However, without having secured your IT/OT integration, these maintenance activities can put your business at great risk.
Send highly classified information over the Internet
Some information is not intended for everyone to see. But how do you ensure that only the right people can read the information? The short answer is: encryption. To ensure that you can send confidential information over the Internet, you need a suitable VPN solution.
If you have secured your integration and have a VPN solution in place, protected communication is ensured, and it is possible to send and receive data over unreliable networks while preventing advanced attackers from being able to read or change data.
So how do you choose the right solution? To make your choice, you need to know the classification of the information you want to protect. How sensitive is it? You also need to be aware of whether there are laws or directives that govern how you should handle information security. By asking yourself these questions, you will know what type of solution you need.
Read more about different VPN solutions in our White Paper: How to choose the right VPN solution.

This is how you make a secure IT/OT integration
Have you not secured your IT/OT integration?
Here we have listed 5 steps on how to do it! The method is based on the standard IEC 62443 – a must for those who work with security in OT.
1. Identify the system
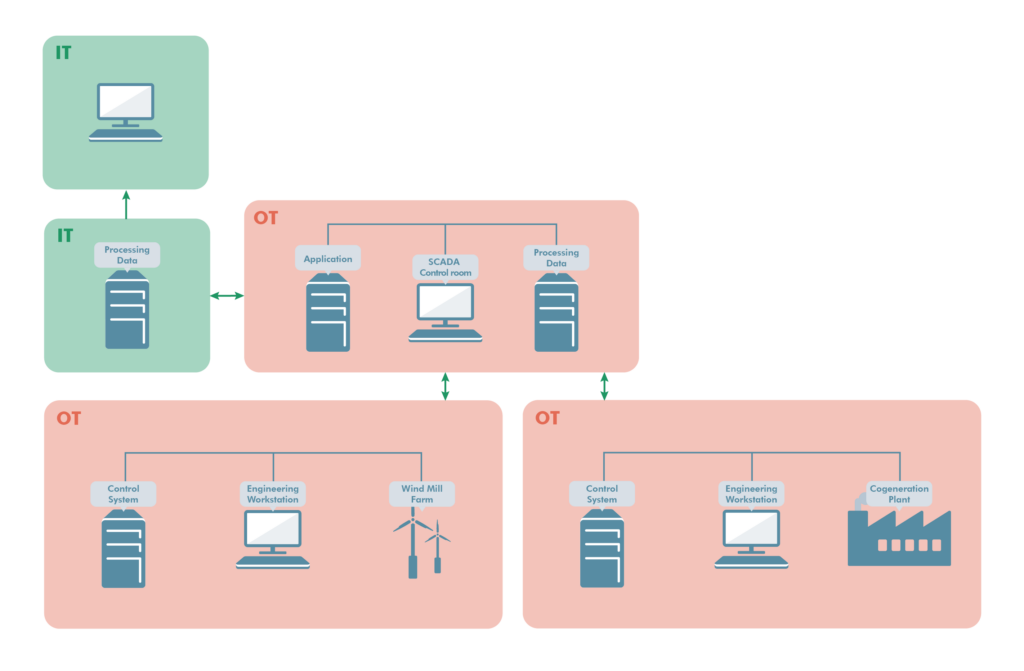
Often there are one or more control systems connected to a SCADA system. This SCADA system contains information that you want to export to the office environment. For example, it could be measured values or statistics from the various processes. You may also need to maintain the OT/SCADA environment and then need to import data from the office environment. When you segment your system, you try to find where the line between IT and OT is – often somewhere between the SCADA system and the office environment.
The main purpose of this step is to scope the project and decide what to segment. It is important to define for the general understanding of the project as an organisation may have many facilities that are integrated with the IT environment. Then it is especially important to map out who should be included and who should not.
2. Initial risk analysis
The next step is to do an initial, simple risk analysis and in it identify the worst that can happen today without having introduced any risk reduction measures. Based on this, you can later make an initial grouping of systems and flows.
You need some input in this phase, such as:
- Overall system architecture
- Risk criteria and risk matrix with tolerable risk – which risks can we accept and what must we fix?
- Existing risk analyses
- Information about the threat picture – what could happen?
Based on this input, you can calculate a worst-case risk that the various parts of the system are exposed to without security functions or segmentation. The question to ask is what impact does a cyberattack that brings systems out of action have on the business? How big will the spread effect be? How large geographical areas are affected and how many people are affected? If, for example, the electricity distribution is shut down, many people could be affected. Are there critical operations (e.g. hospitals) that depend on electricity supply? By placing the scenarios on a scale of consequence level, it becomes clear which scenario is considered the most serious.

3. Zoning and data flows
At this stage, it is important not only to look at the results of the risk analysis, but also to include other factors. What can be a guiding light when segmenting is grouping assets that have the same security level requirements. Base the grouping on the risk analysis, but also on best practices and reference architectures (e.g. Purdue).
When the systems are to be placed in zones, they are divided into, for example, Office, DMZ, SCADA and Facilities. In this analysis, we do not focus on the segmentation between, or within, the facilities. It is outside of IT/OT and is rather about OT/OT segmentation.
When it comes to segmenting data flows, it can be difficult and complex to figure out exactly who they are. When going down to the protocol level, it requires quite detailed technical expertise. You can use traffic analysis to find out exactly which protocols you have and what is going on in the network. One way to do this is to record traffic from your network and then look at the traffic with one or more analysis tools. After carrying out a traffic analysis, you can find out what kind of data is flowing between the zones.
4. Detailed risk analysis
According to IEC 62443, a detailed risk analysis is carried out if the initial risk exceeds the acceptable risk. In the detailed risk analysis, a risk analysis is made per zone and flow. The same risk matrix and method should be used as in the initial risk analysis and this blog text will only go further with the flows and zones that lie between IT and OT. In the detailed analysis, a number of steps are followed:
- Identify threats and threat actors against zones and flows
- Identify vulnerabilities in zones and flows that can be exploited
- Assess unmitigated risks
- Before risk-reducing measures
- Assess reduced risk
- Is the reduced risk acceptable? If not, face more measures.
When the reduced risk falls below the acceptable risk, you have reached your goal with your risk reduction measures and can move on to the next step.
5. Design
After completing the detailed risk analysis, it is time to focus on design. The design is the result of our analysis – here we see what the final segmentation solution will look like. One solution to ensure that the data flow is unidirectional out of the zones is to use data diodes. For example, you can create a unidirectional export channel of measurement data using a data diode.
The IEC 62443 standard defines five security levels that help derive security-related requirements and dial in the strength of the segmentation solution. If you want to work with security in OT, this is a great document to have as a guiding light when building your solution!
Do you want help with how to secure your IT/OT environment? Do you need advice on which products your company needs? Welcome to contact us!




